Gab Security Vulnerabilities
NOTE: This is solely for educational purposes.
Jump to
Discovery
The new year has brought even more memorable events in American politics. This week alone saw the President being permanently banned from Twitter which, paired with the perceived fall of social platform Parler, has caused a large migration to Gab. With this in mind, I started checking the platform out and found some vulnerabilities along the way.
Open URL Redirect Vuln
When scrolling through the timeline, the platform shows trending news sources. When hovering over one of these links, I took note of the format of the destination links.
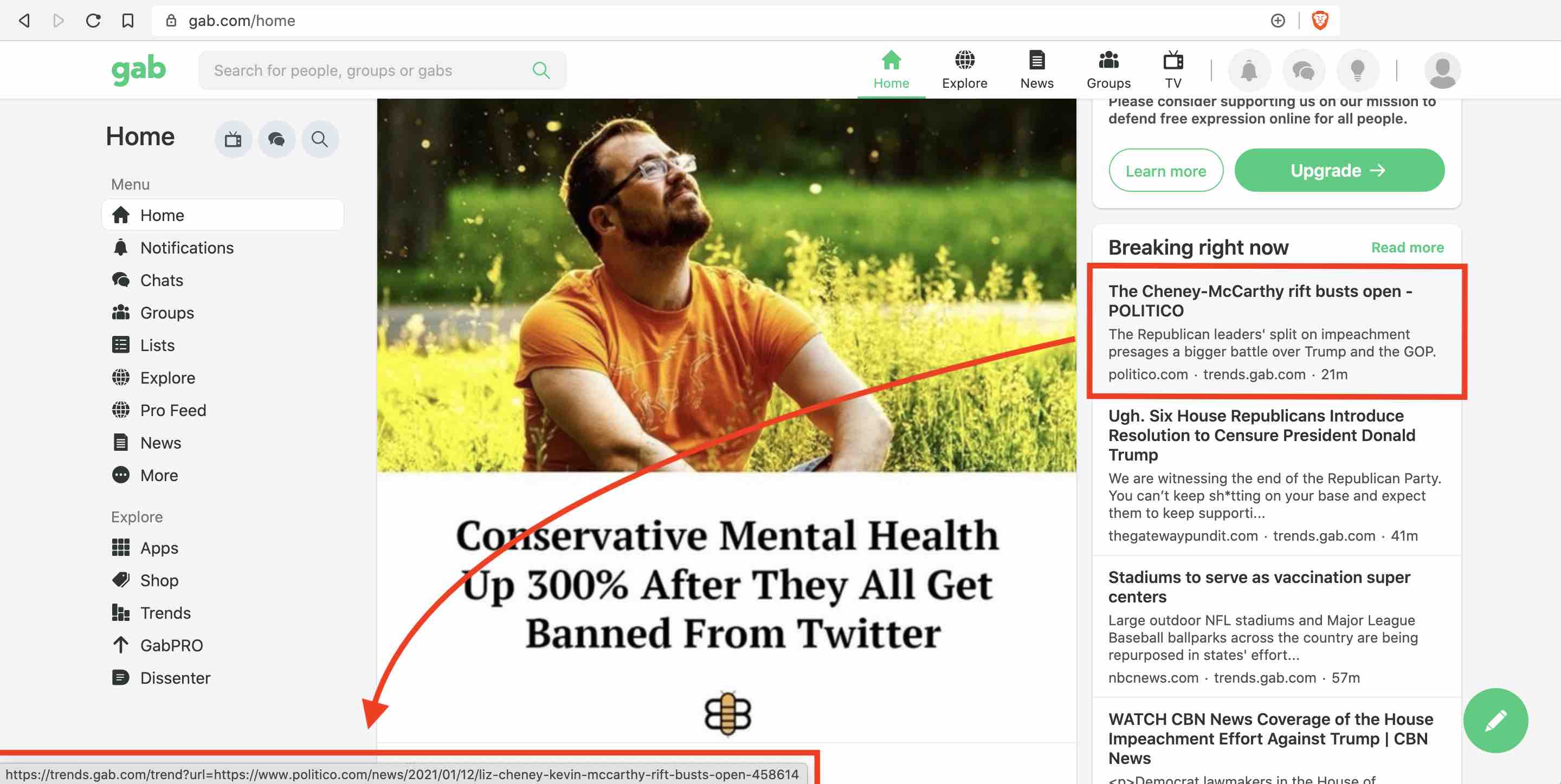
They follow the form https://trends.gab.com/visit?url={destination-url}, where passing the destination URL causes Gab to redirect the user to the destination web page. To test whether the redirect is open, we can craft a URL to redirect us wherever we want and, if it takes us there, the redirect is open. Since https://trends.gab.com/visit?url=https%3A%2F%2Fexample.com directs us to example.com, this is a classic Open Redirect vulnerability. With this, we can trick victims into visiting malicious web pages, since we can make the link look like it's a trustworthy Gab link.
XSS Vuln
After messing with the open redirect URLs above, I was curious as to what the homepage of trends.gab.com looks like.
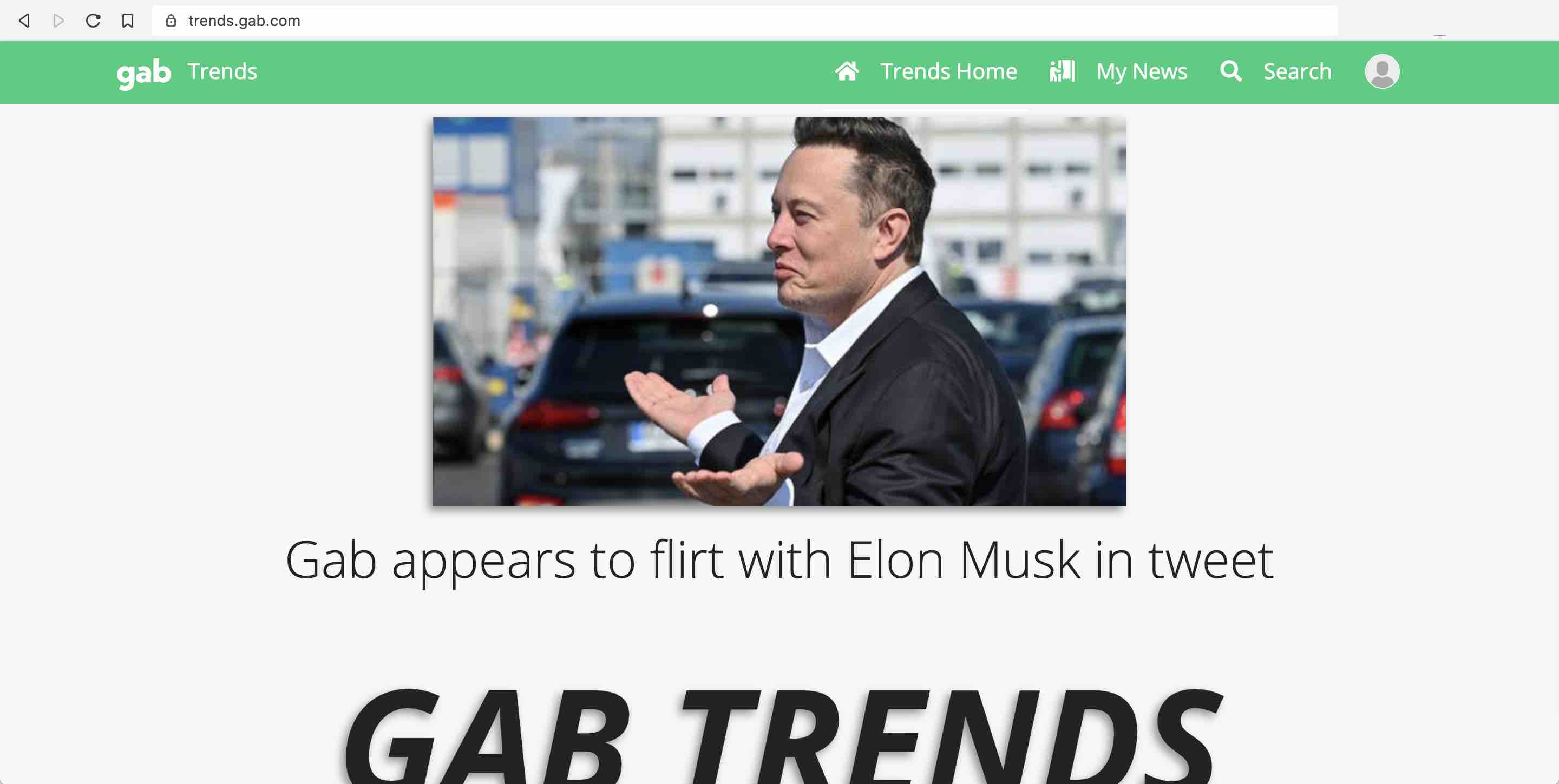
When you visit one of these trend links, you're brought to a page like this, where the article's title and description are displayed.
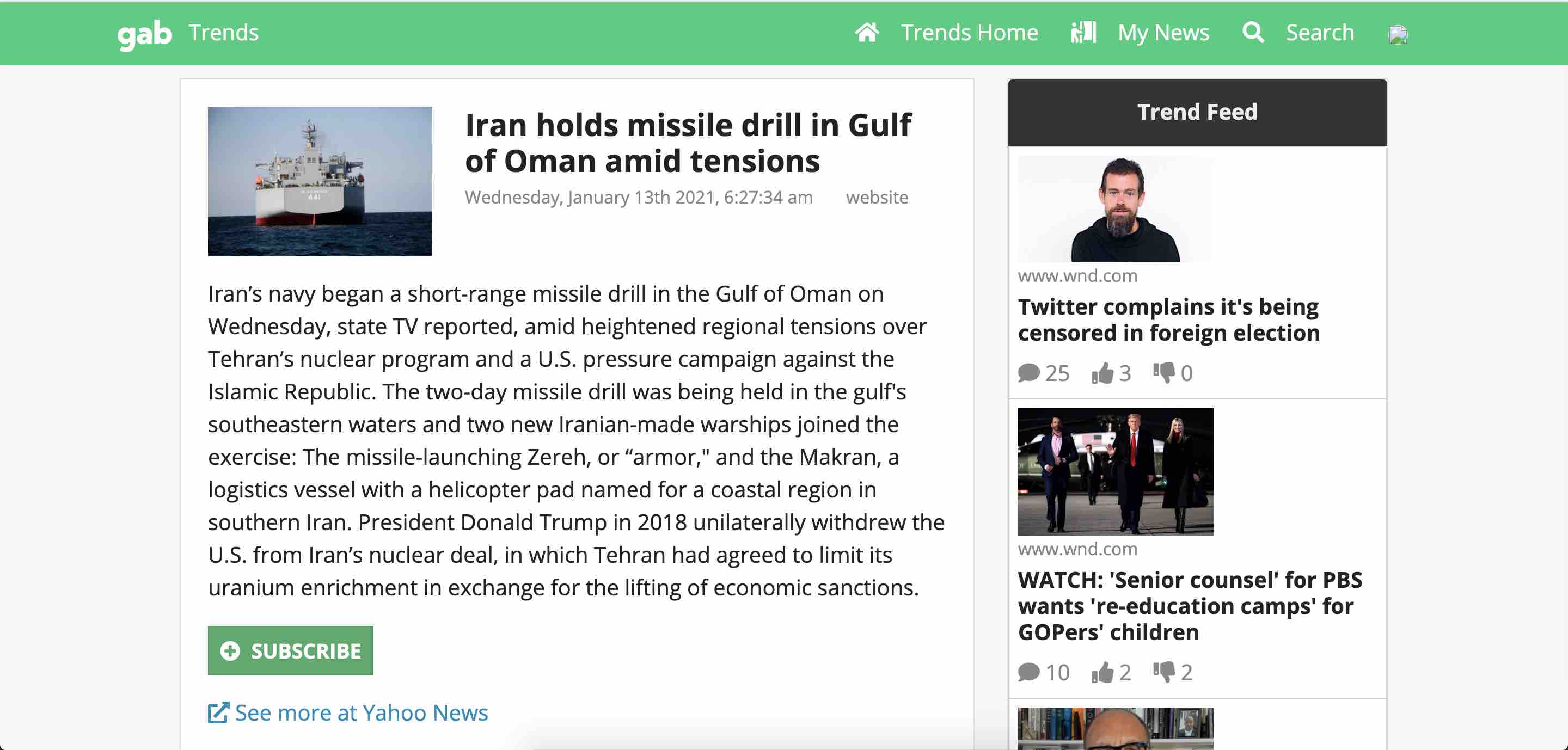
I was curious as to how these articles get added to Gab as trends and learned that any authenticated user can create them. With this in mind, I wanted to see if I could perform a Cross-Site Scripting (XSS) attack by crafting a webpage that injects JavaScript into the Gab preview through its title and description. Long story short, Gab injects whatever metadata description the target page has in its HTML head.
The above web page looks like this on Gab. Notice the prompt in front of the preview page.
This shows that we can run arbitrary code on Gab's trends page. So can we wreak havoc? Eh.
(Not) Increasing Impact
With XSS at our disposal, we have the same control of the browser context as Gab, since we can edit the DOM, add cookies, redirect, etc.
I'd originally tested the app to see whether I could use the XSS vulnerability to perform Cross-Site Request Forgery (CSRF) make new posts on behalf of the user or even delete their account when they visit a malicious trend, and everything was working out until the modern browsers saved Gab.
All of Gab's origins return wildcards in the Access Control Allow Origin (ACAO) header, meaning that any web page can make a request to them. However, modern browsers block cross-origin requests when credentials: 'include' is used and the corresponding ACAO response value is a wildcard in order to prevent CSRF attacks. They got lucky.
With control of the browser context but an inability to forge requests to the more interesting gab.com origin, we're left with the ability to phish Gab users for sensitive information. We can craft an attack such that we exfiltrate the victim's username, profile picture, IP address and more for our record.
We can also load some malware if we know of any active browser zero-days, but I'm not aware of any at the moment. So, I won't be doing that.
Proof of Concept
Who cares about all these words? Show me the demo, right? Gotcha.
Here's a demo where I use a malicious trend to prompt the user for their email and password to be stored for later. I chose prompting for brevity's sake. I could also make a fake login page that steals credentials for a more convincing scheme.
Notice how I redirect the victim to a legitimate trend after grabbing their information. In doing this, I lessen the risk of a victim actually visiting my malicious website, which would raise suspicion since the site may not have any real information.
I can even artificially make my trend post show in the top trends list simply by automating requests to the page. That way, I can gain more victims who think that it's a legitimate trend. This is because HTTP requests alone increment a trend's view counter, and views and recency are used to give priority on the trend lists.
Conclusion
These are only moderately severe vulnerabilities alone, but when chained with functionality of Gab's platform or any other vulnerabilities, a lot of damage can be done.